Install ArgoCD on K8s
Introduction
ArgoCD is a popular tool used for continuous delivery of Kubernetes applications. With ArgoCD, you can deploy your applications to Kubernetes clusters with ease. In this blog post, we will guide you through the process of setting up ArgoCD from scratch and deploying your first app.
Install ArgoCD
kubectl create namespace argocd
kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
## Change the argocd-server service type to LoadBalancer
kubectl patch svc argocd-server -n argocd -p '{"spec": {"type": "LoadBalancer"}}'
## Get the external IP
kubectl get svc argocd-server
## Visit the ArgoCD UI from the browser with external IP above
## Login
argocd admin initial-password -n argocd
## Get password
kubectl -n argocd get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -d
## CLI login
argocd login <ARGOCD_SERVER>
## Change password
argocd account update-password
## Create user
argocd login <ARGOCD_SERVER> --username <USERNAME> --password <PASSWORD>
argocd account list
# if you are managing users as the admin user, <current-user-password> should be the current admin password.
argocd account update-password --account <name> --current-password <current-user-password> --new-password <new-user-password>
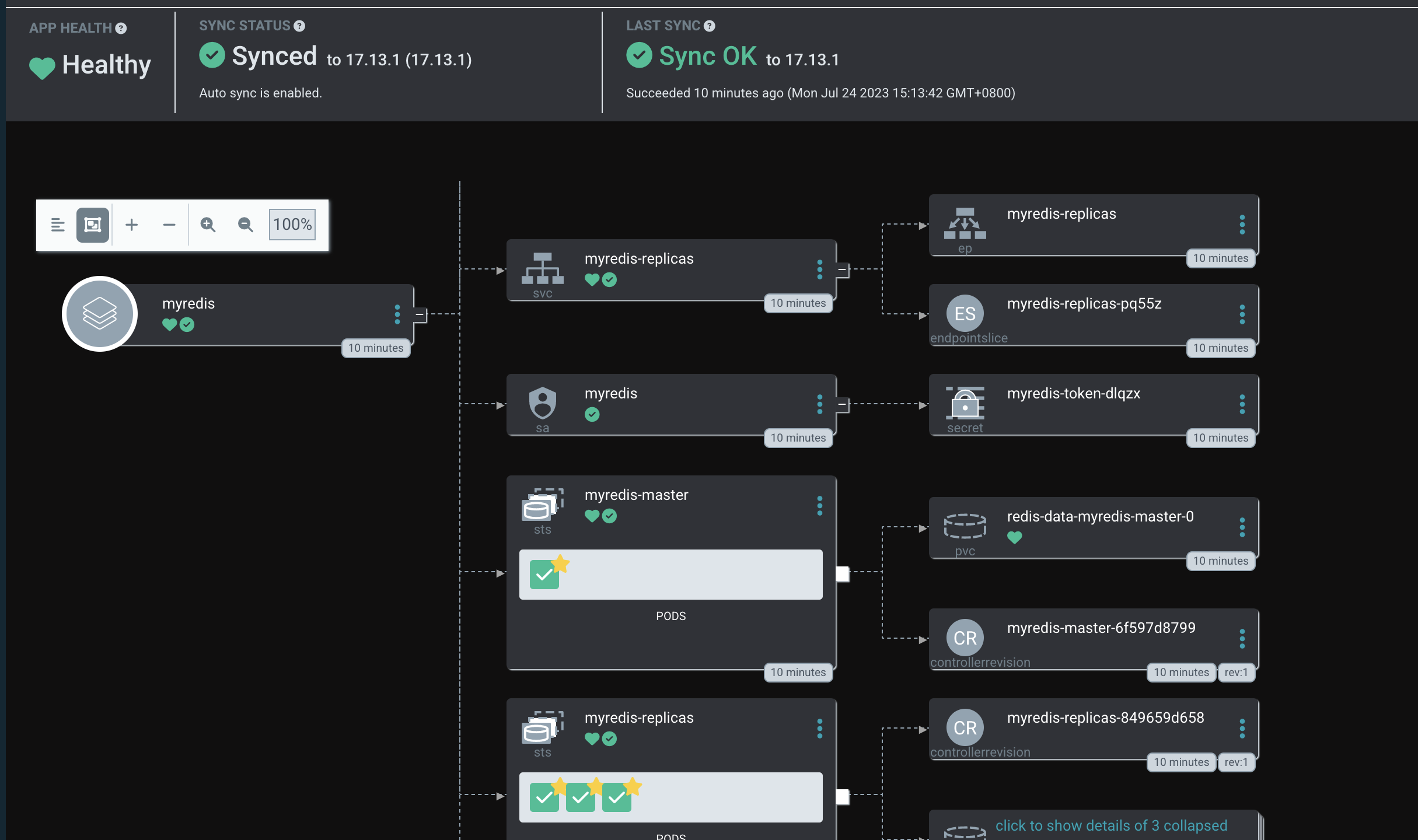
Create your first APP from Web
Cloud use bitnami Helm repo as Source to quickly get started (https://charts.bitnami.com/bitnami).
Create your first APP from CLI
argocd login --core
kubectl config set-context --current --namespace=argocd
argocd app create guestbook --repo https://github.com/argoproj/argocd-example-apps.git --path guestbook --dest-server https://kubernetes.default.svc --dest-namespace default
argocd app get guestbook
argocd app sync guestbook
Accessing Argo CD UI
Port forward
kubectl port-forward svc/argocd-server -n argocd 8080:443
ALB Ingress
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: argocd-ingress
namespace: argocd
annotations:
alb.ingress.kubernetes.io/actions.ssl-redirect: '{"Type": "redirect", "RedirectConfig":{ "Protocol": "HTTPS", "Port": "443", "StatusCode": "HTTP_301"}}'
alb.ingress.kubernetes.io/backend-protocol: HTTPS
alb.ingress.kubernetes.io/certificate-arn: arn:aws:acm:us-east-1:<account-id>:certificate/<certificate-id>
alb.ingress.kubernetes.io/group.name: prodalb
alb.ingress.kubernetes.io/listen-ports: '[{"HTTP": 80}, {"HTTPS": 443}]'
alb.ingress.kubernetes.io/load-balancer-name: shared-load-balacer-name
alb.ingress.kubernetes.io/scheme: internet-facing
alb.ingress.kubernetes.io/tags: Environment=dev,Team=Cool Product, name=ALB
Dev , UsedIN=EKS
alb.ingress.kubernetes.io/target-type: ip
finalizers:
- ingress.k8s.aws/resources
spec:
ingressClassName: alb
rules:
- host: argocd.example.net
http:
paths:
- path: /
backend:
service:
name: argocd-server
port:
number: 443
pathType: Prefix
kubectl apply -f argocd-ingress.yaml
Best Practices for Using ArgoCD
Here are some best practices to keep in mind when using ArgoCD:
- Always use version control for your Kubernetes manifests.
- Use ArgoCD’s built-in validation to catch errors before deploying.
- Use ArgoCD’s rollback functionality to quickly revert changes if necessary.
Setting up an HA installation
- API server: Handles all external interactions. Whether you’re using the CLI, UI, or creating a client, you’ll communicate with the API. The HA manifests set up two instances of this pod.
- Repository server: Responsible for creating the final manifests to apply to the cluster. Manifest generation is complex due to Argo CD’s support for various templating systems like Helm 2 or 3, Kustomize, and Jsonnet. The HA manifests provide two replicas.
- Application controller: Initiates work, implements the control loop, and manages application sync. While initially limited to one instance, it now supports one instance per cluster shard. The HA manifests use a single controller instance.
- Redis cache: Stores generated manifests to avoid expensive recalculations. If the cache fails, it can be rebuilt, but expect a performance hit. The HA setup introduces significant changes here, adding an HAProxy deployment and three Redis replicas—one master and two slaves.
- Dex server: Handles user authentication for external identity providers such as SAML, OIDC, or LDAP. It’s optional but necessary if you want to connect services like GitHub or Google accounts to Argo CD.
argo-cd:
crds:
install: false # Set to false if argo-cd was installed previously
keep: false
configs:
params:
reposerver.parallelism.limit: 4
controller.status.processors: 20 # Set as needed
controller.operation.processors: 10 # Set as needed
controller.repo.server.timeout.seconds: 60 # If managing many repositories, consider increasing this value
timeout.reconciliation: 180s # Polling time
repoServer:
replicas: 2
autoscaling:
enabled: true
minReplicas: 2
maxReplicas: 5
env:
- name: ARGOCD_GIT_ATTEMPTS_COUNT
value: "3"
- name: ARGOCD_EXEC_TIMEOUT
value: "2m30s"
extraArgs:
- --repo-cache-expiration=1h
controller:
replicas: 2 # Consider increasing deployment size if managing many repositories
env:
- name: WORKQUEUE_BUCKET_SIZE
value: "500"
- name: ARGOCD_RECONCILIATION_JITTER
value: "60"
- name: ARGO_CD_UPDATE_CLUSTER_INFO_TIMEOUT
value: "60" # In seconds
- name: ARGOCD_CLUSTER_CACHE_LIST_PAGE_SIZE
value: "500"
- name: ARGOCD_CLUSTER_CACHE_LIST_PAGE_BUFFER_SIZE
value: "5"
server:
autoscaling:
enabled: true
minReplicas: 2 # Should not be 1
maxReplicas: 5
env:
- name: ARGOCD_API_SERVER_REPLICAS
value: "2" # Recommended to be consistent with minReplicas, not less than minReplicas
- name: ARGOCD_GRPC_MAX_SIZE_MB
value: "200"
dex: # Argo's own in-memory storage component, HA mode will cause data inconsistency, can set replica count to 1
enabled: true
redis-ha:
enabled: true
Access Control
Admin and local users
kubectl -n argocd get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -d
argocd account list
add new user
apiVersion: v1
kind: ConfigMap
metadata:
name: argocd-cm
data:
accounts.alina: apiKey, login
argocd account update-password --account alina --current-password pOLpcl9ah90dViCD --new-password k8pL-xzE3WMexWm3cT8tmn
kubectl get secret argocd-secret -n argocd -o yaml
Service accounts
WIP
Single sign-on
Other Deployment Tools
| Tool | Lizenz | GitHub Stars | Ease of Use | UI | Commercial Support | Templating | Deployment |
|---|---|---|---|---|---|---|---|
https://github.com/cdk8s-team/cdk8s |
Apache 2.0 | 3.9k | ⭐⭐⭐⭐ | ❌ | ✅ | ✅ | ❌ |
https://github.com/kubernetes/kubectl |
Apache 2.0 | 2.6k | ⭐⭐⭐⭐ | ❌ | ❌ | ❌ | ✅ |
https://github.com/glasskube/operator |
LGPL.v3 | 152 | ⭐⭐⭐⭐ | ✅ | ✅ | ✅ | ✅ |
https://github.com/helm/helm |
Apache 2.0 | 25.3k | ⭐⭐⭐ | ❌ | ❌ | ✅ | ✅ |
https://github.com/kubernetes-sigs/kustomize |
Apache 2.0 | 10.2k | ⭐⭐⭐⭐ | ❌ | ❌ | ✅ | ✅ |
https://github.com/fluxcd/flux2 |
Apache 2.0 | 5.5k | ⭐⭐⭐ | ✅ | ✅ | ❌ | ✅ |
https://github.com/argoproj/argo-cd |
Apache 2.0 | 14.9k | ⭐⭐⭐⭐ | ✅ | ❌ | ❌ | ✅ |
https://github.com/stefanprodan/timoni |
Apache 2.0 | 981 | ⭐⭐⭐⭐⭐ | ❌ | ❌ | ✅ | ❌ |
https://github.com/carvel-dev/carvel |
Apache 2.0 | 325 | ⭐⭐⭐ | ❌ | ❌ | ✅ | ❌ |
https://github.com/pulumi/pulumi |
Apache 2.0 | 18.4k | ⭐⭐⭐⭐ | ❌ | ✅ | ✅ | ❌ |
https://github.com/hashicorp/terraform |
BSL | 39.8k | ⭐ | ✅ | ✅ | ✅ | ✅ |
https://github.com/grafana/tanka |
MIT | 2.1k | ⭐⭐ | ❌ | ❌ | ✅ | ❌ |
https://github.com/dhall-lang/dhall-kubernetes |
Apache 2.0 | 600 | ⭐⭐⭐ | ❌ | ❌ | ✅ | ❌ |
Conclusion
Setting up ArgoCD and deploying your first app may seem daunting at first, but with this guide, you should be able to do it with ease. Remember to follow best practices when using ArgoCD to ensure a smooth deployment process. Happy deploying!
Reference
https://argo-cd.readthedocs.io/en/stable/getting_started/- argocd CLI:
https://github.com/argoproj/argo-cd/releases/tag/v2.7.8 https://github.com/argoproj/argocd-example-appshttps://medium.com/@megaurav25/argocd-ha-setup-for-production-da38cbb8behttps://argo-cd.readthedocs.io/en/release-2.5/operator-manual/high_availability/https://docs.daocloud.io/en/amamba/quickstart/argo-cd-HA/https://argo-cd.readthedocs.io/en/stable/operator-manual/high_availability/https://github.com/PacktPublishing/ArgoCD-in-Practice
Some of the content is generated by AI, please be cautious in identifying it.