Network packets debug with tcpdump

When it comes to debugging network issues, analyzing packets is an essential part of the process. One tool that can help with this is tcpdump. Tcpdump is a command-line tool for capturing and analyzing network packets. In this blog post, we will explore how to use tcpdump to debug network packets.
Simple example
tcpdump -c ${package_number} -i eth0 -nn dst port ${PORT} -w FILE.packets
Usage
-iinterface-wwrite for file-ccount-Aprints out every packet’s contents-nBy default tcpdump will translate IP addresses to host names.-nforces it to just print the IP-eIncludes the MAC address that the packet came from-pFilters to only packets to/from your computer’s IP address
Analyzing Packets with tcpdump
After capturing packets with tcpdump, we can analyze them using various options and filters. Here are a few examples:
- To display captured packets in real-time, we can use the
noption to display IP addresses instead of hostnames, and thevvvoption to display more verbose output:
sudo tcpdump -i [interface] -n -vvv
- To filter packets based on a specific protocol, such as HTTP, we can use the following command:
sudo tcpdump -i [interface] -w [filename.pcap] tcp port 80
In this command, the tcp port 80 filter specifies that we only want to capture packets that use the HTTP protocol on port 80.
- To filter packets based on a specific IP address, we can use the following command:
sudo tcpdump -i [interface] -w [filename.pcap] host [ip address]
In this command, the host [ip address] filter specifies that we only want to capture packets to or from the specified IP address.
10 Useful tcpdump examples
Capturing Traffic on a Specific Interface
i anymeans all the interfaces.
tcpdump -i ens160
tcpdump -i any
Capturing IP-Host Specific Packets
tcpdump -i ens160 -c 5 host 140.240.61.21
Capturing Packets on a Specific Port
tcpdump -i any port 8000
Writing Packets to a File (w)
tcpdump -c 5 -w network_file_linux.pcap -i any
Capturing Packets from a Specific Protocol
tcpdump -i ens160 -c 5 -nn tcp
Filtering tcpdump Packets from Specific Source & Destination Host
tcpdump src 100.10.8.121
tcpdump dst 14.211.62.121
Rotating tcpdump Packets
tcpdump -i ens160 -w /tmp/network-%H-%M.pcap -W 48 -G 300 -C 100
- C file_size (M) G rotate_seconds W filecount
tcpdump -G 100 -W 3 -w network-%H-%M.pcap port 19096
1 root wheel 384881 Feb 13 17:09 network-17-08.pcap
1 root wheel 2096619 Feb 13 17:11 network-17-09.pcap
1 root wheel 320744 Feb 13 17:13 network-17-11.pcap
Capturing Multiple Hosts with tcpdump
tcpdump src 192.168.0.10 or src 192.168.0.10
Filtering Multiple Ports with tcpdump
tcpdump -i eth0 port 22 or port 9402
Filtering All Interfaces
tcpdump -i any
tcpdump -i eth0 arp or icmp and host 192.168.0.10
Tcpdump Command Options Summary
Tcpdump provides several options that enhance or modify its output. The following are the commonly used options for the tcpdump command.
| Option | Description |
|---|---|
-i |
Listen on the specified interface. |
-n |
Don’t resolve hostname. You can use -nn to not resolve hostname or port names. |
-t |
Print human-readable timestamp on each dump line, -tttt: Give maximally human-readable timestamp output. |
-X |
Show the packet’s contents in both hex and ASCII. |
-v, -vv, -vvv |
Enable verbose logging/details which among other things will give us a running total on how many packets are captured. |
-c N |
Only get N number of packets and then stop. |
-s |
Define the snaplength (size) of the capture in bytes. Use -s0 to get everything, unless you are intentionally capturing less. |
-S |
Print absolute sequence numbers. |
-q |
Show less protocol information. |
-w |
Write the raw packets to file. |
-C file_size(M) |
Tells tcpdump to store up to x MB of packet data per file. |
-G rotate_seconds |
Create a new file every time the specified number of seconds has elapsed. |
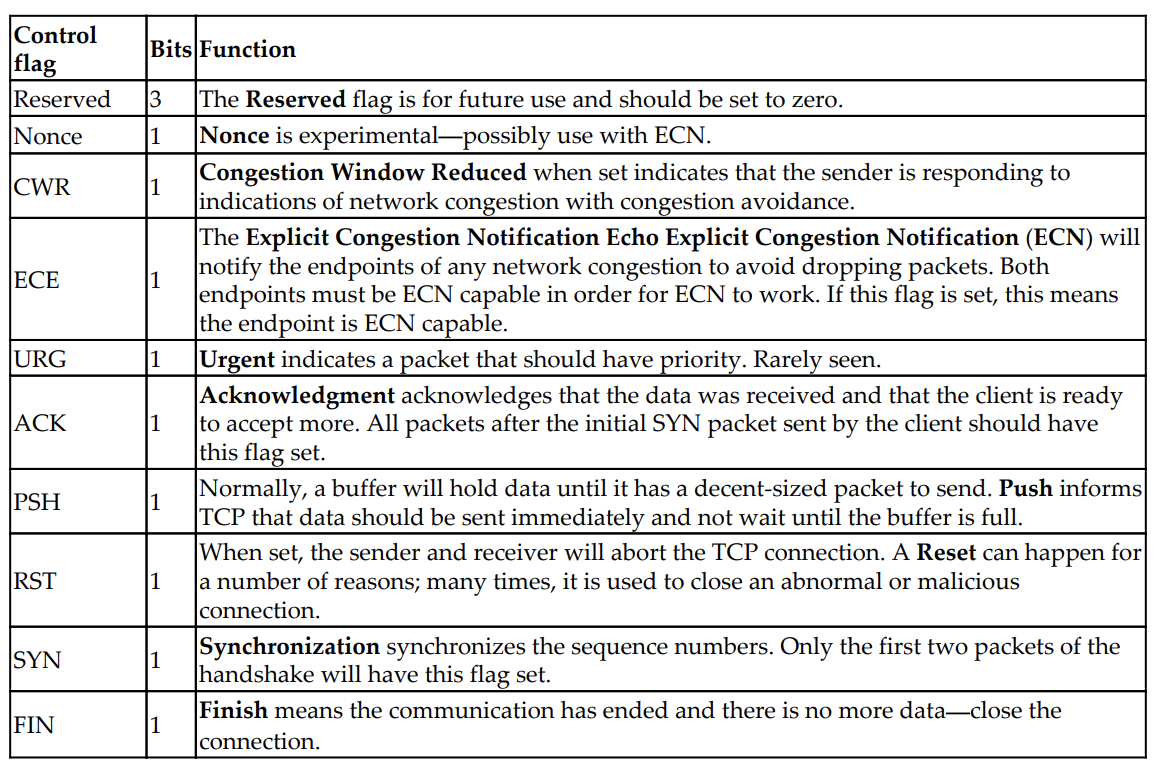
TCP Control Flag
Reference
https://wizardzines.com/zines/tcpdump/