Infrastructure as Code
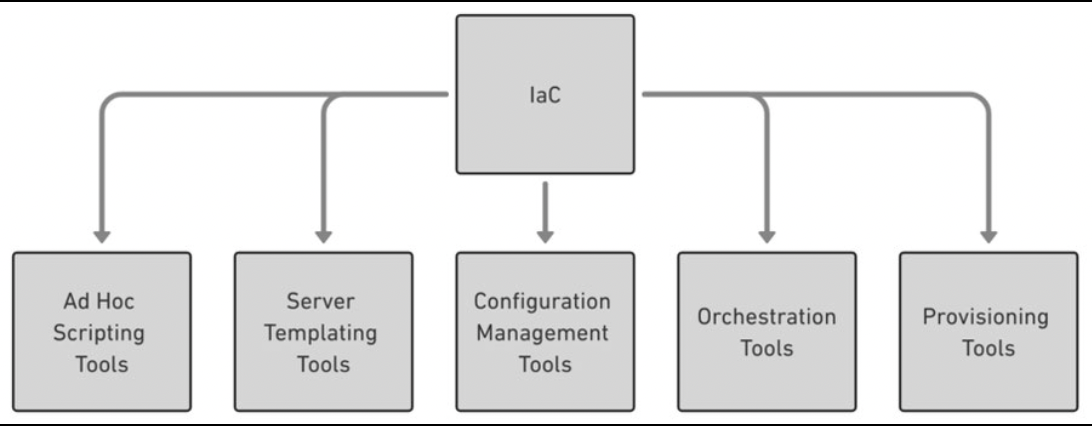
Introduction
Infrastructure as Code (IaC) is an approach to managing and provisioning IT infrastructure through the use of code and software development techniques. In other words, it means automating the process of configuring and deploying infrastructure using software tools and programming languages. IaC is the latest trend in IT operations and is fast becoming the preferred approach for managing infrastructure in both small and large organizations.
Benefits of IaC
One of the most significant benefits of IaC is its ability to automate processes, which reduces human error and increases efficiency. With IaC, infrastructure can be deployed quickly and consistently, reducing deployment time and ensuring that environments are configured correctly every time. It also enables teams to collaborate better, as IaC allows for version control and other software development practices that make it easier for teams to work together.
- Speed: Infrastructure as Code (IaC) tools allow you to create resources much faster compared to manually navigating through multiple screens. For instance, recreating an environment for a critical application due to unforeseen circumstances can take hours if done manually, but an IaC tool can accomplish this in minutes.
- Consistency: IaC tools enable the creation of identical environments repeatedly, minimizing the risk of errors that can occur when done manually.
- Traceability: IaC tools require a configuration file to create an environment, allowing for easy tracking and versioning in a source code system like AWS CodeCommit or GitHub. This history can assist fellow developers in reviewing changes.
- Cost Reduction: Manual creation of resources requires human effort each time. Automation with IaC tools eliminates this need, reducing associated costs.
- Customizability: IaC tools are customizable, with parameters that can be passed at runtime to tailor them for specific environments. For example, you can launch two instances of an EC2 instance in your development environment and ten in production by passing these values as parameters.
- Reduced Risk: IaC automation produces consistent results each time, reducing the risk of human error and potential outages due to misconfiguration.
- Standardization: IaC tools can enforce and standardize security practices and other organizational standards. These can be linked to an approval process, providing visibility into changes in your environment.
- Self-Documentation: IaC tools self-document, explaining how your infrastructure was created and when changes were made. This eliminates the need for explicit documentation for new team members.
Implementing IaC
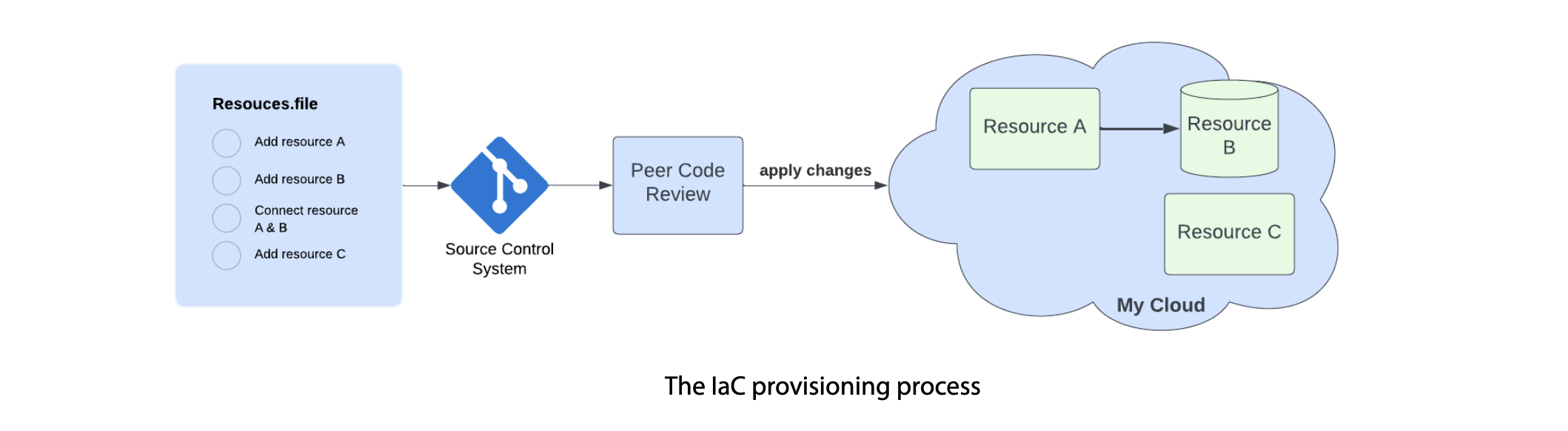
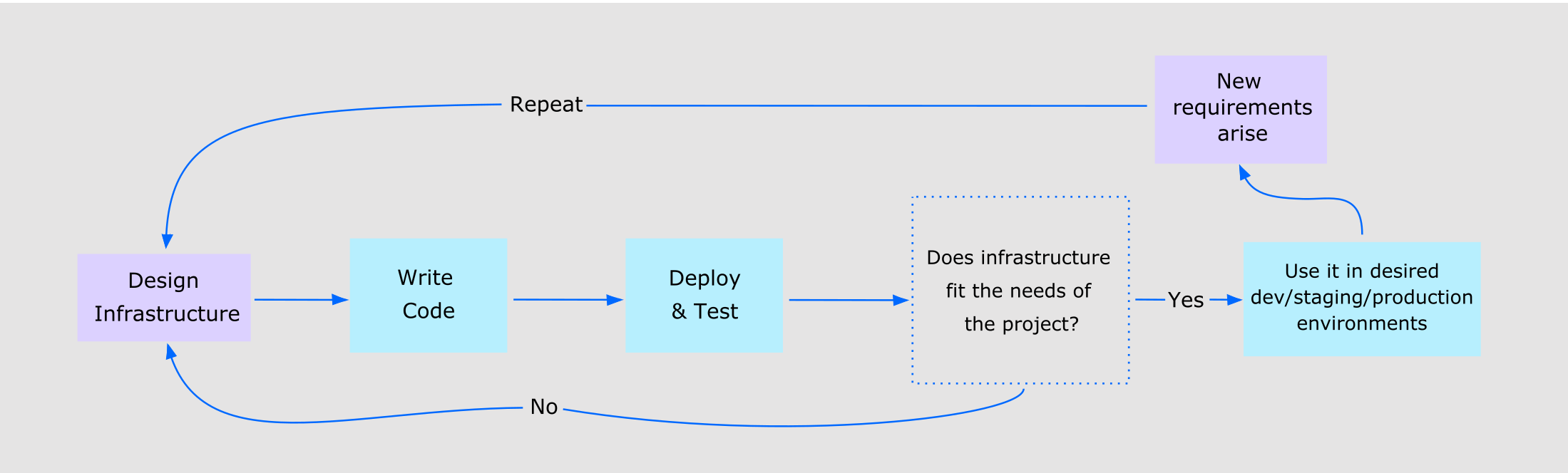
Implementing IaC requires a shift in mindset, as it involves treating infrastructure as a software project. This means that infrastructure must be designed, versioned, and tested like any other software. Teams must also adopt DevOps practices to ensure that they can effectively manage IaC. This includes using continuous integration and continuous delivery (CI/CD) pipelines to automate the deployment process, and using tools like Puppet, Chef, and Ansible to manage infrastructure as code.
| IaC tools | Provider |
|---|---|
| AWS CloudFormation | Amazon Web Services |
| Google Cloud Deployment Manager | Google Cloud Platform |
| Azure Resource Manager | Microsoft Azure |
| Bicep | Microsoft Azure |
| HashiCorp Terraform | HashiCorp |
| Pulumi | Pulumi |
| AWS Cloud Development Kit | Amazon Web Services |
| Kubernetes manifests | Kubernetes (container orchestrator) |
Terraform
Main commands:
init Prepare your working directory for other commands
validate Check whether the configuration is valid
plan Show changes required by the current configuration
apply Create or update infrastructure
destroy Destroy previously-created infrastructure
All other commands:
console Try Terraform expressions at an interactive command prompt
fmt Reformat your configuration in the standard style
force-unlock Release a stuck lock on the current workspace
get Install or upgrade remote Terraform modules
graph Generate a Graphviz graph of the steps in an operation
import Associate existing infrastructure with a Terraform resource
login Obtain and save credentials for a remote host
logout Remove locally-stored credentials for a remote host
metadata Metadata related commands
output Show output values from your root module
providers Show the providers required for this configuration
refresh Update the state to match remote systems
show Show the current state or a saved plan
state Advanced state management
taint Mark a resource instance as not fully functional
test Execute integration tests for Terraform modules
untaint Remove the 'tainted' state from a resource instance
version Show the current Terraform version
workspace Workspace management
Conclusion
Infrastructure as Code is the future of IT operations, and its benefits are numerous. By automating infrastructure deployment and management, organizations can achieve greater efficiency, reliability, and scalability. However, implementing IaC requires a shift in mindset and the adoption of DevOps practices. Organizations that embrace IaC will be better positioned to succeed in today’s fast-paced, constantly evolving IT landscape.
References
- Infrastructure as Code: What Is It and Why Should You Care? (
https://www.digitalocean.com/community/conceptual-articles/infrastructure-as-code-explained) https://www.terraform.iohttps://aws.amazon.com/cloudformationhttps://www.pulumi.com- Azure Infrastructure as Code (
https://learn.microsoft.com/en-us/azure/azure-resource-manager/templates/overview) https://dev.to/aws-builders/create-mongodb-atlas-cluster-with-terraform-and-aws-51d8https://dev.to/aws-builders/how-to-manage-aws-security-hub-in-aws-organizations-using-terraform-5gl4https://medium.com/google-cloud/build-infrastructure-on-google-cloud-with-terraform-google-challenge-lab-walkthrough-30a592373d3ehttps://cloud.google.com/blog/products/devops-sre/infrastructure-as-code-with-terraform-and-identity-federation/https://dev.to/aws-builders/my-service-mesh-journey-with-terraform-on-aws-cloud-part-1-3heehttps://dev.to/lordamola/provisioning-multiple-aws-rds-instances-with-terraform-5237https://dev.to/chinmay13/aws-networking-with-terraform-hosting-a-static-website-using-s3-4683https://medium.com/@amitmavgupta/cilium-azure-rke2-terraform-lets-call-it-cart-f4c0b8dadf4ehttps://www.hashicorp.com/blog/manage-your-infrastructure-lifecycle-with-new-terraform-packer-waypoint-and-nomadhttps://dev.to/damdev95/a-step-by-step-guide-to-easily-deploying-eks-infrastructure-and-applications-using-terraform-g1https://ralph-allison.medium.com/implementation-of-an-e-commerce-system-on-aws-in-an-automated-way-using-terraform-and-ansible-4dd541816c85https://auth0.com/blog/get-started-with-auth0-terraform-provider/https://medium.com/@nik2701k/aws-vpc-peering-with-terraform-3010eccfb8fehttps://dev.to/tythos/accessible-kubernetes-with-terraform-and-digitalocean-12ohttps://dev.to/env0/using-terraform-kubernetes-and-helm-the-power-trio-52o7https://medium.com/@devops-ousmanou/guide-complet-pour-la-mise-en-place-dune-infrastructure-sur-aws-avec-terraform-3c2acd8b050fhttps://dev.to/codeisgood/invoking-an-aws-lambda-function-with-terraform-3nl7https://sysadminxpert.com/managing-terraform-state-file-on-s3/https://www.ntweekly.com/2024/04/03/deploy-gcp-infrastructure-using-terraform-and-azure-devops-pipelines/https://aws.amazon.com/blogs/containers/streamline-production-grade-clusters-with-amazon-aft-and-terraform-eks-blueprints/https://dev.to/rinaxsumomo/importing-existing-aws-iam-resources-to-terraform-1dachttps://aws.amazon.com/blogs/architecture/how-zurich-insurance-group-built-their-scalable-account-vending-process-using-aws-account-factory-for-terraform/https://dev.to/suzuki0430/optimizing-s3-bucket-management-and-lifecycle-with-terraform-45nehttps://thenewstack.io/introduction-to-infrastructure-as-code/
Some of the content is generated by AI, please be cautious in identifying it.